Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

A comprehensive guide explaining Linux file permissions and how to manipulate them.
Image courtesy: studiogstock on Freepik
One of the reasons why Linux is considered one of the most secure operating systems is because of the way how security is implemented at each layer within its multi-user architecture. UNIX (predecessor of Linux) originated in the era of mainframes where there was a single central computer to which multiple users could connect using terminals which provided an interface to interact with the system. As it was very crucial to keep each of these user information secure from access by another user the operating system has to be secure and the way to accomplish this was to have these functionalities baked right into its core. And thus at the core of these features is the file permission system. And because Linux is based on UNIX these security features are inherently available. If you are interested in knowing the origins of Linux/Unix and their history you can check this blog in which I’ve discussed this topic in-depth and also covered other related concepts.
If you are a system admin, a developer, or anyone who works with Linux-based systems understanding these file permissions and how to play around with them using a terminal is crucial. In this blog post, I will take you through an in-depth exploration of how Linux file permissions work, how to interpret them, and how to manage them effectively. So are you ready? Yes? So let’s get started. 😀
In Linux, every file and directory is associated with a set of permissions. These permissions determine who can read(r), write(w), or execute(x) the file or directory. Permissions are broken down into three categories:
Each of these categories has three types of permissions as given below:
Here one thing to note is that ‘Execute’ permission is needed to enter the directory. Having only Read / Write will not allow you to enter the directory and thus create new sub-directories within that directory.
Linux file permissions are represented by a series of ten characters in the output of the ls -l command. For example:
-rwxr-xr--
Here’s how to interpret these characters:
- for a regular file.d for a directory.l for a symbolic link.b for a block device.c for a character device.p for a pipe.s for a socket.rwx) represent the permissions for the owner of the file.
r means read permission.w means write permission.x means execute permission.r-x) represent the permissions for the group.
r means read permission.- means no write permission.x means execute permission.r--) represent the permissions for others (everyone else).
r means read permission.- means no write permission.- means no execute permission.So, in the example -rwxr-xr--, the file is a regular file where:

To change the permissions of a file or directory, we can use the chmod (change mode) command. There are two main ways to set permissions with chmod: (1) symbolic mode and (2) numeric mode.
In symbolic mode, you specify the permissions using letters. For example:
mohit@hyperfoss:~$ chmod u+x file.txt
This command adds execute permission (x) for the user (u).
You can also combine changes:
mohit@hyperfoss:~$ chmod g+w,o-r file.txt
This command gives write permission (w) to the group (g) and removes read permission (r) from others (o).
In numeric mode, permissions are represented by three octal digits, where each digit is the sum of the values for read (4), write (2), and execute (1):
Let’s say we want to apply a ‘read’ and ‘execute’ permission to a file, to do that the number we need to use is 4 + 1 = 5 which in binary is 101, similarly for ‘write’ and ‘execute’ this would become 2 + 1 = 3 which in binary is 011.
For example, to give the owner full permissions (7), the group read and execute permissions (5), and others only read permissions (4), you would use:
mohit@hyperfoss:~$ chmod 754 file.txt
This command sets the permissions to -rwxr-xr--.
For example, 7 translates to 111, 5 to 101 and so on. Now if I pass 754 it effectively translates the file permission as below:
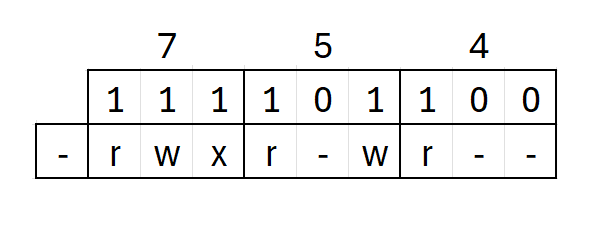
The choice between numeric or symbolic mode simply depends upon personal preferences. I like the symbolic mode over the numeric mode, but in some literature, you’ll also find the numeric mode being used extensively.
In addition to changing file permissions, you can also change the ownership of a file or directory using the chown and chgrp commands.
chown (change owner): Changes the user and/or group ownership of a file or directory.
mohit@hyperfoss:~$ sudo chown user:group file.txt
This command changes the owner of file.txt to user and the group to group.
chgrp (change group): Changes only the group ownership of a file or directory.
mohit@hyperfoss:~$ sudo chgrp group file.txt
This command changes the group ownership of file.txt to group.
Changing the permission on the file is not the end of the story. Linux provides an extra bit that could be set/unset for managing some special permissions, that offer more control over executable files and directories:
SUID (Set User ID): When set on an executable file, this permission allows users to execute the file with the file owner’s privileges. For example, the passwd command typically has the SUID bit set so that any user can change their password.
To set SUID:
mohit@hyperfoss:~$ chmod u+s file.txt
SUID is represented as an s in the owner’s execute position: -rwsr-xr-x.
SGID (Set Group ID): When set on a directory, this permission ensures that files created within the directory inherit the group ownership of the directory, not the user’s primary group.
To set SGID:
mohit@hyperfoss:~$ chmod g+s directory
SGID is represented as an s in the group’s execute position: drwxr-sr-x.
Sticky Bit: Typically used on directories, the sticky bit ensures that only the owner of a file can delete or modify it, even if other users have write permissions to the directory.
To set the sticky bit:
mohit@hyperfoss:~$ chmod +t directory
t in the others’ execute position: drwxr-xr-t.Let’s go through some practical examples to reinforce the concepts:
Example 1: Allow a Group to Edit a File
Suppose you have a file project.txt and you want the group developers to be able to read and write to it, but not execute it.
mohit@hyperfoss:~$ sudo chgrp developers project.txt
mohit@hyperfoss:~$ sudo chmod 664 project.txt
Now, project.txt will have the permissions -rw-rw-r--.
Example 2: Secure a Shared Directory
Let’s say you have a shared directory /shared/projects where multiple users can collaborate. You want to make sure that only the file owner can delete files, but everyone in the projects group can add and modify files.
mohit@hyperfoss:~$ sudo mkdir /shared/projects
mohit@hyperfoss:~$ sudo chgrp projects /shared/projects
mohit@hyperfoss:~$ sudo chmod 2775 /shared/projects
mohit@hyperfoss:~$ sudo chmod +t /shared/projects
The directory will now have the permissions drwxrwsr-t.
To conclude:
Whether you’re setting up a secure server, managing a multi-user system, or simply working on your own projects, mastering Linux file permissions is an essential skill. The file permission system in Linux is a powerful and flexible technique that provides you with deeper control access to files and directories. If you understand how to read and modify these permissions, you can effectively manage your system’s security and ensure that users have the appropriate levels of access, without causing harm.
I hope this deep dive into Linux file permissions has provided you with the required knowledge to confidently manage permissions on your Linux systems. If you have any questions or additional insights, feel free to share them in the comments below! Also don’t forget to read ‘Most Essential Linux Commands’ which will surely add some useful tools to your Linux command toolbox.